I had a list of projects which a nice, long European holiday vacation was sure to inspire, this is what it consisted of. We enjoyed the wonders of the season.. a few short-lived visitors, and a lot of 'new family' fun (way, way, way.... more than expected); followed by a week or so of hard work, and a few more days off. It is now just a wish-list of which ideas are still to come. As far as other, planned blog posts, as time allows, there is a whole notebook full of that, as well!
-Setup Roblox and play that with junior cherokeejb, including some packet-fun (complete, and analysis in progress). I was really amazed about the breadth of attacks out there also regarding the game; there was some write-ups about hijacking the related chat application, and even some network anaylsis projects in progress on github.
-Setup 2 new Internet Storm Center honeypots (* we did also start at least, this!)
-share the audio ("nice background study/hack music") from the lounges which I streamed and dumped live during the 34c3 last week (need to check around the community to see if a good free host, e.g. on the hackint.org or one of the chaos locals' websites); otherwise include this on the BSides Soundcloud project, started with Springfield, but is soon spreading to all the conferences.
-post a walkthrough of the old SANS network forensics poster excersizes
-finish and share the remaining videos from BSides Springfield (did make some progress on this as well, and many of the videos are finished, just waiting for the correct release order) - note to self next year make sure to have a video mixer
-setup github and publish some small OSX production scripts and link to other projects I am using to improve skills, done
-post initial thoughts of completing "Cyber Operations... building, defending, and attacking modern computer networks" by Mike O'Leary, and on the initial skim of "blue team field manual" . We are reading "Cyber..." in our book club, and David even had the author in to the main/USA conference call. I highly recommend this book, and it sounds like the cyber defense program at Townsend is also off the charts.
-post at least one of the disk forensics write-ups I'd already been working on (did start even more, made a friend friends happy... zero write ups :) * note to self, just write in real time on each study night from here on. Similarly, Bryan shared today a great write-up regarding foremost, as well, this post is from Raj Chandel.
-finish the first round of setup of "infosecfeeds.org" planet website for infosec podcasat, this keeps always getting pushed to the side, but if I had time would be fun to use to play more with AWS as well as xml formatting (to rss, atom, etc.)
-do a simple osx disk forensics, "recovery" for the average user blog (*a certain friend of mine would also be very happy about this!) - did not do yet
-Share the research so far on the mysterious "Unauthentic" OSX (malware?) that I was discussing on the BrakeSec Slack #Malware channel (* this will for sure be the next post after Roblox networking monitoring post ...look for it!). I had some amazing support on the malware channel regarding this post. I did make some packet captures, and review some data from prior captures; and found some really interesting stuff, that may be partially related. I was really amazed at how it may have came from the so-called Hola VPN / Zon networks /luminetti (p2p malware essentially), here is an amazing write-up by Vectra labs. I also dove into the "Mac Defender" family of malware and Proton family malware because of this. Such interesting work...
...well, with a new baby in the house, priorities shifted a bit, but I did have a ton of fun, and at least we did setup Roblox (packet snorting and all), and that is a fun, on-going family project, look for a post on that soon as well. I caught a few episodes of the American tv show "scorpion". I must say, just when you think you're starting to learn a few things... there's always someone out there with more blinky blinky on their computer screens! just kiddng ,well... at least we got our priorities straight!
*Happy Holidays everyone*
JB's Security blog: Researching, looking to get to the deepest level, and documenting topics I find interesting in Security. If you use Linkedin, please also subscribe at https://www.linkedin.com/today/author/cherokeejb
Saturday, January 13, 2018
The 3 Mac security tips for Managers (and everyone) - #offtopic
The 3 Mac security tips for Managers (and everyone)
...aka "Macs don't get viruses... oops, not really!" -
Managers, artists, teachers, and just about anyone else can follow these tips to make your Mac a security tank!
Combine these 3 tips with regular updates of your computer and applications and prudent web-browsing (think especially of blocking un-needed ads or other javascript) to make your Mac as strong as a castle or a tank - This is an archive & git copy of the most important ways people can secure their Macintosh computers.
Part 1: Use a regular user account.
These tips also apply to Microsoft Windows and Linux/Unix. If you follow these tips, it will make your computer run more quickly and much more safely, and keep you in line with your IT Policy at work as well as policies of other organizations you may visit.
If you operate your computer as a normal user, (you may hear this referred to also a a non-privileged user, non-admin user, or similar), you will literally reduce your chance of most types of security-related problems with your computer, by over 80%. I've seen reports that put this even as high as 95%! The smartest IT minds in the world agree with this tip: here is a very easy-to-read report from the ASD, and if you want to go down the security rabbit hole, see also these older reports from the UK's NCSC, and America's NSA.
Hopefully, all of your company's computers are already setup this way. To make this change on your personal computer, it is super easy, and if I find a nice Youtube video for you, I will come back and post it here, or even make one myself someday.
Feel free to grab a tea with me and have a nerdy chat, or share with me your favorite new music and films, at any time. Reach out!
Part 2: Don't install apps outside of the Apple "App Store."
Here is the next instalment of "Mac's don't get viruses (oops... not really!)"
This tip also applies Linux and other Unix systems with their "repositories"--even Windows is largely moving in this direction--there is an official "Windows Apps" store now, which is growing quickly, programs like Microsoft Office have moved largely to online versions.
So this will prevent you from getting almost 100% from any type of malware, even viruses, or even the new-fangled "ransomware" which I'm sure many of you have heard about lately. The tip is as simple as this: do not click any warnings that pop-up on your computer that something "is not signed," and never change the settings under System Preferences > Security & Privacy > General, lower than the middle setting, as shown in this image. Leave this at the top setting if possible, and only if needed for popular 3rd-party programs like Adobe Suite or Avid's Pro Tools or Media Composer, select the middle/2nd setting. Never use the 3rd choice.
Hopefully, all of your company's computers are already setup this way. To make this change on your personal computer, it is super easy, and if I find a nice Youtube video for you, I will come back and post it here, or even make one myself someday. If you're interested in the meantime, I recommend this blog! Have a nice one!
Part 3 - DO NOT USE PASSWORDS FOR MORE THAN ONE THING!"
Here's the last edition of our 3-part-series of tips to make your computer run better for you, and protect yourself online.
These days, tips like this are not even optional-- they'll keep you in line with your IT Policy at work and other companies--and even more importantly protect your personal relationships, your creative assets such as your music or film files, and as you'll see today, even your money!
Does that title look like screaming ;-) ...it is. Friendly screaming, albeit.
Q: How can I fix this problem? A: Don't use the same password for anything important. That's it.
In a recent interview I did on the Brakeing Down Security Podcast (sic) several of the top Security professionals in Europe, which I interviewed that day, agreed that ironically password reuse was the biggest problem facing organizations today, because of how it may lead to so many other risks. One person even suggested to do away with passwords completely in favor of something new.
If you want to hear some of the worst IT-scare-stories I've ever seen, read this about locking people out of there Apple stuff, or this about losing your life savings while buying a house. These are most simply the result of... yup, password reuse.
You don't have to take my word for it: take a look at online databases of leaked passwords, and search for an old e-mail address, or a friend's e-mail address (*for security, please don't use your own, current e-mail addresses).
If you have trouble making up good passwords, then use a software password manager, like LastPass or KeePass. As well if you store anything really valuable to you or your company, online, then use an un-related 2nd factor for logging in. Better yet don't store private or important things online at all! Feel free to come to me with questions like this, at any time.
...This concludes my series of how to easily secure your Mac. Like I mentioned in the Introduction, if you combine these 3 tips with regular updates of your computer and applications and prudent web-browsing (think especially of blocking un-needed ads or other javascript) it will make your Mac safe against almost anything that would come it's way. Thanks for reading, and contact me with any comments or questions !
---
---
notes:
This was adapted from a company newsletter and used in production/"security awareness training" which I wrote at a former employer. This was also shared on my new github account that I mention below, so feel free to use the text from here, or there in your own security awareness trainings or newsletters.
I'm in the process this weekend of setting up a new github account, for personal use; to keep things separate from a few project sites, and mostly to share sysadmin scripts I've written in production for some recent new job applications in process. I also hope to use the site to fork python projects and other code that I might hopefully work on for fun and learning, sooner than later.
Subscribe to:
Comments (Atom)
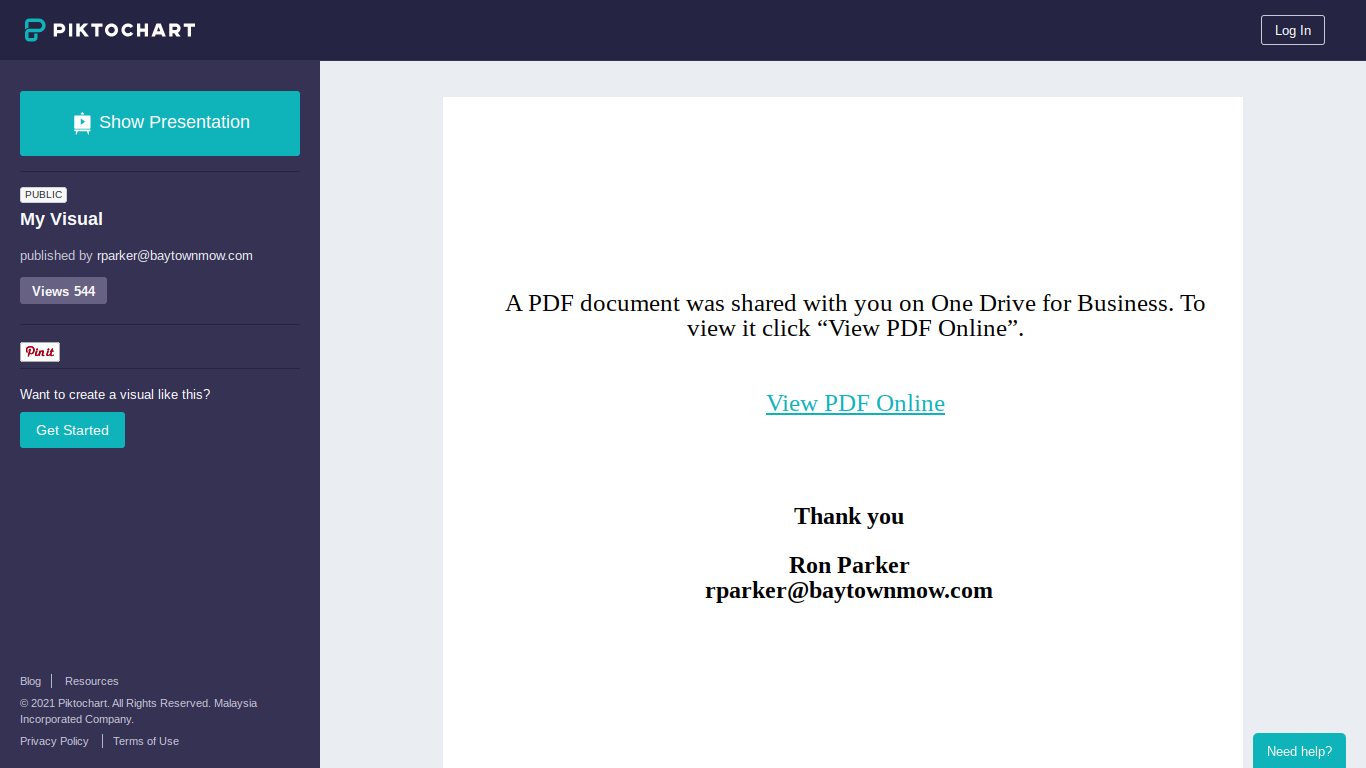
Piktochart - Phishing with Infographics (Guest diary on Sans Internet Storm center - isc.sans.edu)
Noticed today I'd forgotten to re-post this guest diary I shared to Storm center. Link to original post , My most recent work hasn...
-
Noticed today I'd forgotten to re-post this guest diary I shared to Storm center. Link to original post , My most recent work hasn...
-
A lof of work has went into these... and protecting our countries from harm This looks a lot nicer at https://www.linkedin.com/pul...
-
I'll be mostly focusing the next several months on MacOS malware and any new or innovative threats and defenses that come up. I'll ...


